Lora in five questions
This is a brief overview of Lora and LoraWAN. We tried to compile a set of FAQ and answer them in a single place. If you are interested for more information please contact TTN Melbourne group or contact the author.
- What is the idea behind Lora, e.g. LPWAN?
- Where does Lora fit compared to other wireless technologies?
- How much data can I send and What is a typical range?
- What is a typical Lora network topology and how does it work?
- How Secure is Lora?
What is the idea behind Lora, e.g. LPWAN?
LPWAN (Low Power Wide Area Network) offers low power sensors and applications that need to send small amounts of data over long distances a few times per hour and need to last long time on a single battery, theoretically for years. Comparison of LPWAN to LAN and Cellular is given next
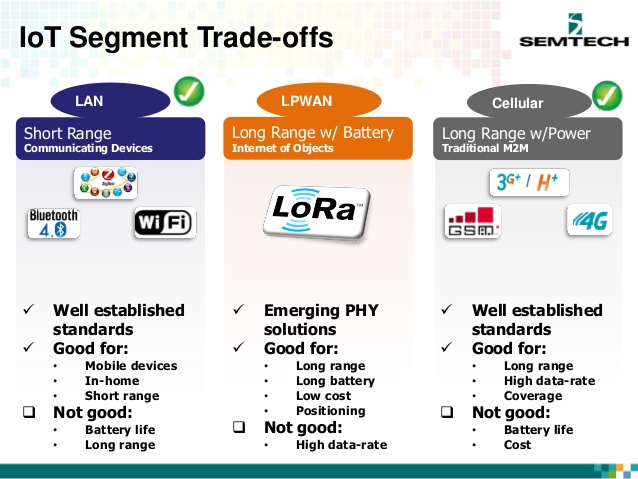
As it can be seen LPWAN technologies are useful for applications that require
- Long range
- Long battery life
- Low Cost
- Positioning
However LPWAN are not designed for high data transmission capabilities. It is expected that LPWAN technologies will cover almost 50% of IoT communications in the future as shown in the following table.
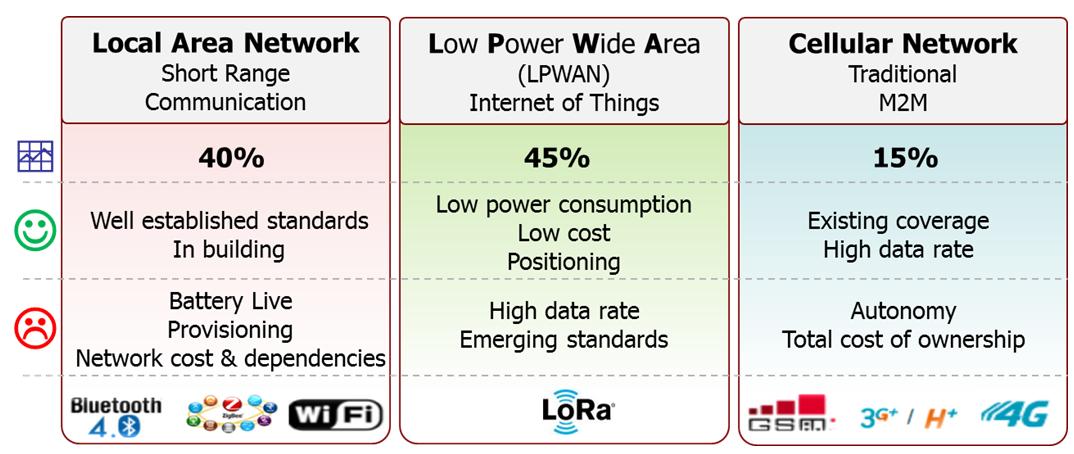
Some possible applications are: pet tracking
- Smoke alarm
- water meter
- Trash container
- Vending machine
- Gas monitor
More are added and can be found at Use cases.
Where does Lora fit compared to other wireless technologies?
Lora is a LPWAN solution along with others such as SigFox, Telensa, PTC, etc. Generally these technologies have varying range and data transmission rate but they aim to support over 10kms. The following diagram compares wide variety of technologies based on the coverage.
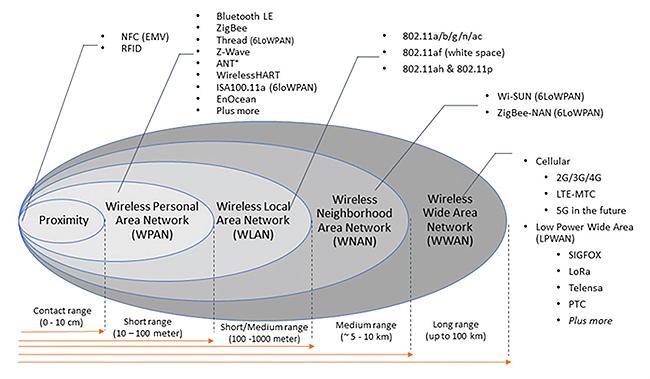
How much data can I send and What is a typical range?
Lora supports 2-3km range in urban and 10-15km in rural areas. The transmission rate of Lora is between 300bps to 50kbps. Following diagram compares bandwidth and range of different technologies.
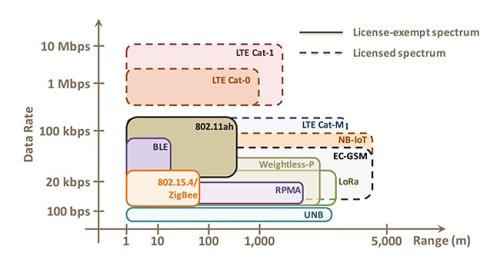
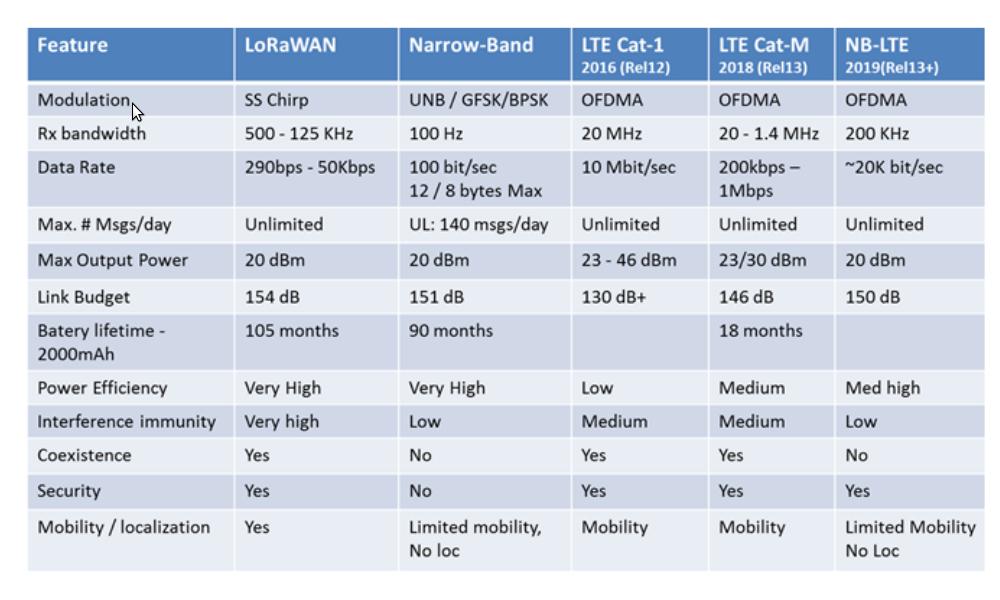
A more technical detail is given below.
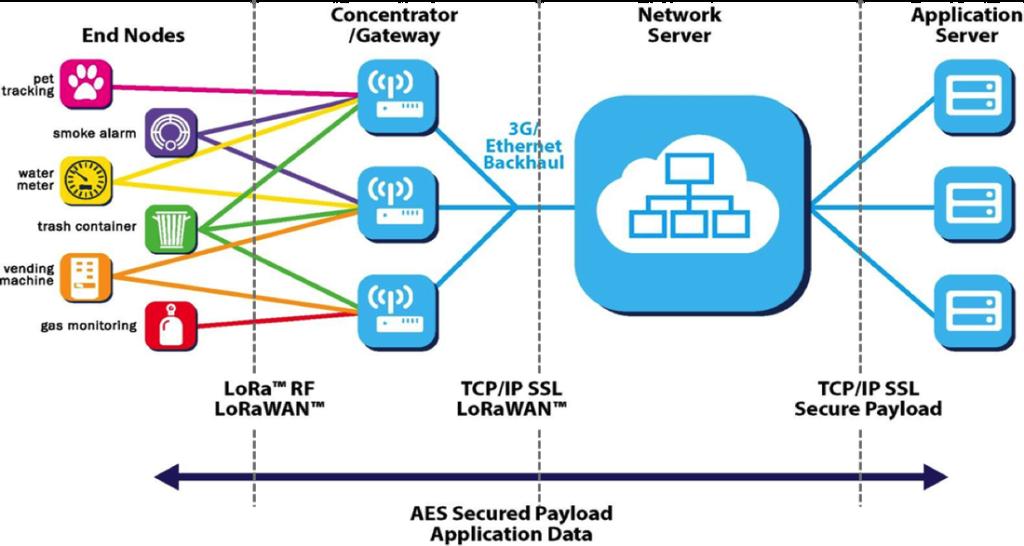
What is a typical Lora network topology and how does it work?
In a LoRaWAN™ network nodes (sensor devices) are not associated with a specific gateway. Instead, data transmitted by a node is typically received by multiple gateways. Each gateway will forward the received packet from the end-node to the cloud-based network server via some backhaul (either cellular, Ethernet, satellite, or Wi-Fi). The intelligence and complexity is pushed to the network server, which manages the network and will filter redundant received packets, perform security checks, schedule acknowledgments through the optimal gateway, and perform adaptive data rate, etc. Finally the network server redirects the data to the associated application servers.
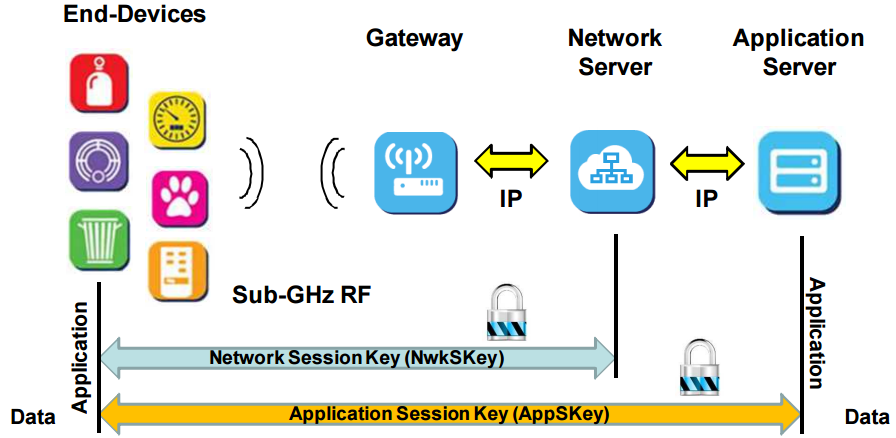
How Secure is Lora?
The LoRaWAN uses two keys to provide security to its connected devices:
- Unique Network key
- Unique Application key
The network key is used to provide confidentiality between the gateway and the connected device, to ensure that only this gateway knows what the content of the packets are. This provides security until the packet has reached the gateway. The application key is used for encrypting the payload of the packet for end-to-end security between device and application server. Each key is used by AES-128 to encrypted their specific content.
For tighter security encryption at the end point is also possible and AES and CAST5 are found to be suitable to be used with limited resource constrained devices. For details please see More Security